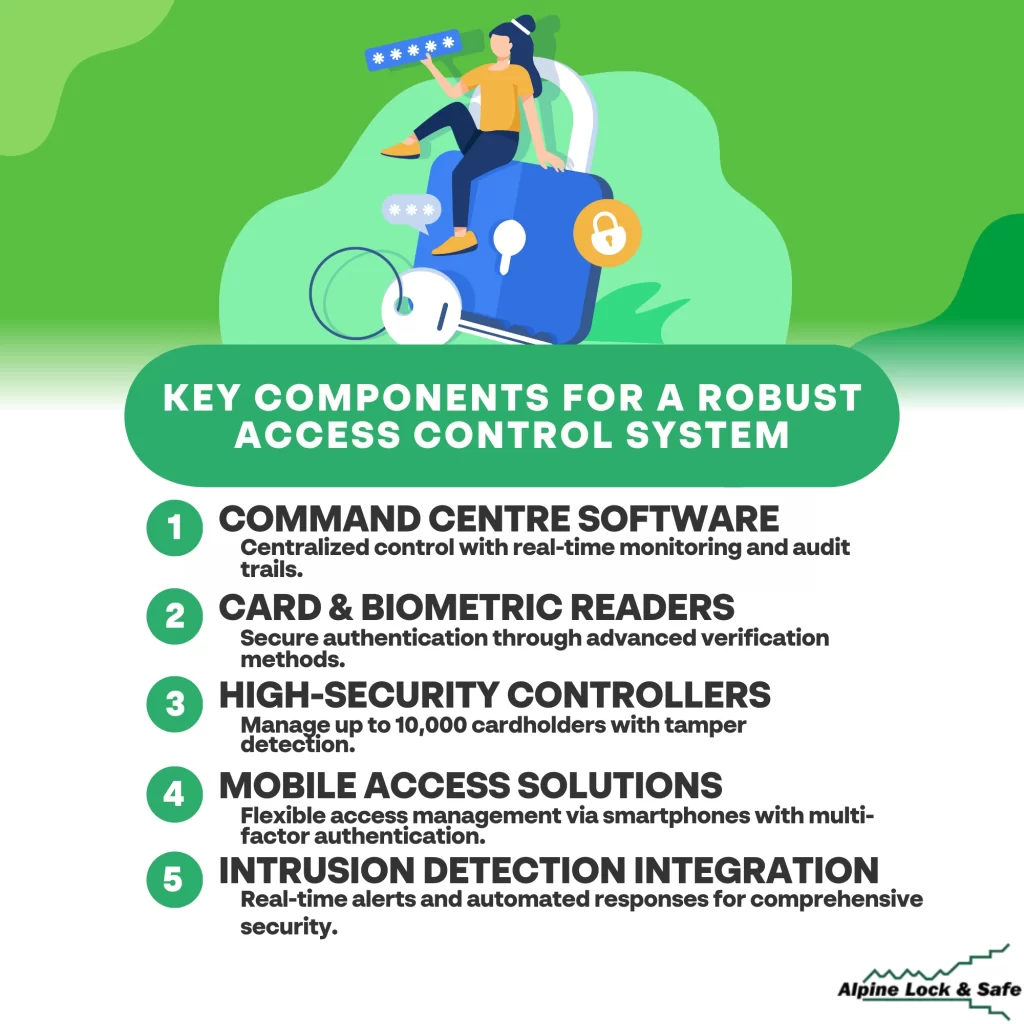
Gallagher’s Access Control System incorporates ten crucial components to improve security and streamline operations. You’ll rely on Command Centre Software for centralized control, Card and Biometric Readers for rigorous authentication, and High-Security Controllers that support up to 10,000 cardholders. Mobile Access Solutions leverage smartphones for flexible entry management, while Intrusion Detection Integration fortifies your defenses. Additionally, Visitor Management systems guarantee efficient entry, and scalability allows seamless growth. Real-time monitoring provides immediate alerts, while robust Cyber Security Features implement advanced encryption and Multi-Factor Authentication. There’s more to uncover about how these components build a thorough security framework.
Key Takeaways
- Command Centre Software: Robust interface for centralized access management, real-time monitoring, and detailed audit trails.
- Card and Biometric Readers: Advanced authentication methods ensure secure, accurate identification and seamless integration with the Command Centre.
- High-Security Controllers: Supports up to 10,000 cardholders, real-time monitoring, and tamper detection for sensitive environments.
- Mobile Access Solutions: Enables flexible access management via smartphones with BLE and NFC, supporting multifactor authentication.
- Intrusion Detection Integration: Enhances security with real-time alerts and collaboration with other security systems for unified protection.
Command Centre Software
Gallagher’s Command Centre Software is the backbone of its access control system, providing a robust and intuitive interface for security management. You’ll find that this software integrates seamlessly with Gallagher access control hardware, offering real-time monitoring and thorough reporting capabilities. The Command Centre’s user-friendly dashboard allows you to manage access points, configure schedules, and set user permissions with precision.
When diving into the specifics, you’ll appreciate that the software supports automated responses to security events, improving your facility’s overall safety. Detailed audit trails are generated, enabling you to track and analyze access attempts, which is vital for compliance and incident investigation. The system’s scalability means it can grow with your organization’s needs, regardless of whether you are managing a single site or multiple locations.
Gallagher access control integrates with third-party systems to provide a complete security solution. The software’s flexibility guarantees it can adapt to various security policies and procedures. For those needing a detailed understanding, an access control system PDF is available, offering in-depth documentation and system specifications. With Gallagher’s Command Centre Software, you are equipped with a data-driven, efficient platform that improves both security and operational efficiency.
Card and Biometric Readers
You’ll find that Gallagher’s card and biometric readers offer advanced authentication methods, guaranteeing robust security. These readers seamlessly integrate with existing systems, minimizing disruption and maximizing efficiency. With precise data handling and compatibility, they improve the overall functionality of your access control infrastructure.
Authentication Methods Overview
When examining the authentication methods within Gallagher’s Access Control System, it is essential to evaluate both card readers and biometric readers. Card readers, typically utilizing RFID or smart card technology, offer a balance between security and convenience. They can store encrypted data, guaranteeing that only authorized personnel gain access. The read range, typically between 2.5 to 10 cm for RFID, makes them suitable for high-traffic environments. However, the risk of card loss or theft remains a concern.
Biometric readers, on the other hand, provide a higher level of security by verifying unique physiological traits such as fingerprints, facial features, or iris patterns. These systems often employ algorithms with False Acceptance Rates (FAR) as low as 0.001%, ensuring accurate identification. The speed of authentication can be under a second, making them efficient for high-security areas. With advancements in liveness detection, modern biometric readers can now differentiate between real traits and spoofing attempts.
Both methods can be integrated with Gallagher’s Command Centre software, allowing for centralized management of access rights and real-time monitoring. While card readers offer simplicity and cost-effectiveness, biometric readers provide unparalleled security, making them indispensable in vital infrastructure.
Integration With Existing Systems
Integrating card and biometric readers into existing systems can greatly improve the overall security framework. When you incorporate Gallagher’s advanced readers, you’re leveraging state-of-the-art technology that seamlessly integrates with your current infrastructure. These readers support multiple authentication methods, including MIFARE, DESFire, and fingerprint recognition, guaranteeing compatibility and boosting security.
Gallagher’s card readers are designed for robust performance, capable of handling high-frequency usage without degradation. They offer encrypted communication protocols, which protect data transmission between the reader and the control system. This guarantees that even if intercepted, the data remains secure and unusable to unauthorized parties.
Biometric readers add another layer of security by utilizing unique physiological traits. Gallagher’s biometric readers are equipped with advanced algorithms capable of processing and authenticating fingerprints in under a second. This minimizes delays and boosts user experience while maintaining stringent security standards. They also integrate effortlessly with existing databases, allowing for seamless data migration and synchronization.
High-Security Controllers
High-security controllers are pivotal components in Gallagher’s Access Control System%20is,%3A%20doors%2C%20gates%2C%20checkpoints.), designed to guarantee the utmost protection for sensitive environments. They utilize advanced encryption algorithms, guaranteeing that all data transmitted between devices and the central system is secure. These controllers support up to 10,000 cardholders and can manage multiple access points, making them versatile for various applications.
You’ll appreciate their real-time monitoring capabilities, which allow for immediate detection and response to security breaches. With dual-network ports, they offer redundancy to maintain system integrity even if one network fails. Additionally, high-security controllers are equipped with tamper detection features, sending alerts if unauthorized access attempts occur.
The controllers are also compatible with Gallagher Command Centre, providing centralized management and seamless integration with other security systems. They support various authentication methods, including biometric readers and smart cards, to suit your specific security needs.
Their robust architecture includes a secure memory module that guarantees data integrity during power outages. The controllers boast an impressive Mean Time Between Failures (MTBF) rate, underscoring their reliability. By incorporating these high-security controllers, you’re investing in a resilient, scalable, and secure access control solution that meets the highest industry standards.
Mobile Access Solutions
Building upon the robust security offered by the high-security controllers, Gallagher’s Access Control System also excels in providing cutting-edge Mobile Access Solutions. With these solutions, you gain the flexibility and security of managing access through your smartphone. Leveraging BLE (Bluetooth Low Energy) and NFC (Near Field Communication), the mobile credentials guarantee encrypted communication, minimizing the risk of unauthorized access.
Gallagher’s Mobile Connect app allows you to issue, manage, and revoke access credentials in real time. This means you can instantly update access permissions without the need for physical key cards, reducing administrative overhead. Additionally, the system supports multifactor authentication, combining mobile credentials with biometric verification, assuring a higher security threshold.
Data from Gallagher indicates a 40% reduction in access-related incidents when organizations switched to mobile access. The app’s user interface is intuitive, designed for ease of use, which translates to faster onboarding and fewer user errors. Integration with existing IT infrastructure is seamless, thanks to Gallagher’s robust API support. This allows for real-time synchronization of user data and access logs, providing thorough audit trails and improving overall security posture.
Incorporating mobile access into your security strategy not only modernizes your approach but also greatly improves operational efficiency and security.
Intrusion Detection Integration
Improving your security landscape, Gallagher’s Access Control System seamlessly incorporates Intrusion Detection Integration to provide an all-encompassing defense mechanism. This sophisticated integration guarantees you’re not only controlling access but also actively monitoring and responding to potential threats in real-time. Here’s how it amplifies your security posture:
- Real-Time Alerts: The system provides instantaneous notifications when a breach is detected. You’ll receive immediate alerts, enabling swift action to mitigate any potential damage.
- Comprehensive Monitoring: With advanced sensors and detectors, it continuously scans for unauthorized access attempts. This guarantees that every corner of your facility is monitored, leaving no room for unnoticed intrusions.
- Automated Responses: The system can be programmed to trigger automatic responses during an intrusion, such as locking down specific areas or sounding alarms. This automation minimizes human error and speeds up response times.
- Detailed Reporting: Post-incident analysis is essential for tightening security protocols. Gallagher’s system logs all events and creates detailed reports, which can be reviewed to understand security gaps and improve future defenses.
Perimeter Security
How can you assure that your facility’s first line of defense is impenetrable? Gallagher’s Perimeter Security solutions provide robust, data-driven methods to secure your facility’s boundaries. Utilizing advanced sensor technology, the system detects unauthorized access attempts in real-time, guaranteeing immediate response to potential threats.
Gallagher’s perimeter security includes electric fencing, which delivers a non-lethal shock to deter intruders. This fencing integrates with the Command Centre software, offering real-time monitoring and control. When a breach is detected, the system can automatically trigger alarms, activate cameras, and notify security personnel, reducing response times considerably.
Fiber optic cable detection is another critical component. Installed along the perimeter, these cables detect vibrations caused by climbing or cutting attempts. The data gathered from these sensors is analyzed to distinguish between genuine threats and environmental noise, minimizing false alarms.
Additionally, Gallagher’s Perimeter Security leverages thermal imaging cameras. These cameras provide high-resolution video feeds, even in low-light conditions, and automatically detect intrusions based on heat signatures. Integration with analytics software allows for precise identification and tracking of suspicious activities.
Visitor Management
In managing visitors, you’ll appreciate Gallagher’s streamlined visitor registration process that guarantees efficient and secure entry. The system’s access badge management allows you to control and monitor visitors’ movements within your facility, providing precise data on their whereabouts. This integration improves security by maintaining a detailed log of all visitor activity.
Visitor Registration Process
Managing visitor registration efficiently is crucial for maintaining security and operational flow within any facility. Gallagher’s Visitor Registration Process guarantees that every visitor is accounted for and authorized before entry. The process is designed to be both robust and user-friendly, leveraging advanced technologies to streamline the visitor experience while fortifying security protocols.
Here’s a breakdown of the fundamental elements:
- Pre-Registration: Visitors can pre-register online, reducing wait times upon arrival. This data-driven approach captures necessary information in advance, facilitating a quicker check-in process and allowing for better planning and resource allocation.
- ID Verification: Upon arrival, visitors’ identification is scanned and verified against pre-registered details. This step utilizes biometric authentication and document scanning to confirm the legitimacy of the visitor’s identity, increasing accuracy and security.
- Host Notification: Once verified, the system automatically notifies the host of the visitor’s arrival via SMS or email. This seamless communication guarantees that hosts are prepared to greet their visitors promptly, enhancing operational efficiency.
- Digital Records: All visitor data is stored securely in a centralized database, providing a thorough audit trail. This real-time logging allows for quick access to visitor history, facilitating efficient tracking and reporting.
Access Badge Management
With respect to enhancing security and operational efficiency, Gallagher’s Access Badge Management system for visitors offers a sophisticated solution. You’ll find it seamlessly integrates with your existing security infrastructure, guaranteeing that visitor management is both secure and efficient. The system allows you to assign temporary access badges to visitors, controlling their movements within predefined areas and time frames.
Gallagher’s system provides real-time updates and audit trails, so you can monitor visitor activity with precision. Each badge is uniquely encoded, reducing the risk of unauthorized access and guaranteeing that every entry and exit is logged. The system supports a variety of badge types, including RFID and smart cards, allowing for flexibility based on your specific requirements.
Data-driven reports generated by the system offer insights into visitor patterns and behavior, helping you optimize security protocols. Integration with other Gallagher components, such as CCTV and intrusion detection systems, provides a thorough security solution. You can also set automated notifications for badge expiry and unauthorized access attempts, enhancing the proactive security measures of your organization.
System Scalability
Gallagher’s Access Control System is designed with scalability at its core, guaranteeing it meets the evolving needs of any organization, regardless of size or complexity. Whether you are managing a small office or a multi-site enterprise, this system scales seamlessly to accommodate your requirements.
- Flexible Architecture: The system’s modular design allows you to add or remove components easily, making certain that it can grow alongside your organization. This flexibility minimizes the need for costly overhauls or system replacements.
- Centralized Management: Gallagher’s system supports centralized management, providing a single interface to control access across multiple locations. This reduces administrative overhead and guarantees consistent policy enforcement.
- Data Handling: Capable of processing high volumes of data, the system guarantees rapid access decision-making even as your user base expands. This robustness is vital for maintaining security without compromising performance.
- Integration Capabilities: The system’s ability to integrate with other security and business systems improves its scalability. By leveraging existing infrastructures, you can expand functionalities without redundancy, optimizing both performance and cost.
Real-Time Monitoring
As your organization scales and complexity increases, maintaining a clear and immediate understanding of onsite activities becomes paramount. Gallagher’s Access Control System excels in providing robust real-time monitoring capabilities, guaranteeing you stay informed about every critical event as it unfolds.
The system’s real-time monitoring feature allows you to view live data feeds from various access points, integrating seamlessly with CCTV footage for thorough surveillance. You’ll be able to track entry and exit logs, employee movements, and unauthorized access attempts instantaneously. By leveraging advanced analytics, the system can identify anomalies and trigger alerts, enabling you to respond promptly to potential security breaches.
Furthermore, Gallagher’s solution supports customizable dashboards that display key performance indicators (KPIs) relevant to your security needs. These dashboards can be customized to show metrics such as the number of active access points, recent security incidents, and user-specific access patterns.
The real-time monitoring also includes mobile access, so you can receive updates and alerts on-the-go via your smartphone or tablet. This guarantees continuous oversight, regardless of your physical location. By utilizing Gallagher’s real-time monitoring, you’re equipped with the data-driven insights necessary to improve your organization’s security posture effectively.
Cyber Security Features
You’ll appreciate that Gallagher’s Access Control System incorporates advanced encryption protocols to protect sensitive data. Real-time threat detection guarantees immediate response to potential breaches, enhancing system reliability. Additionally, multi-factor authentication greatly bolsters user verification, reducing the risk of unauthorized access.
Advanced Encryption Protocols
When it comes to safeguarding sensitive information, robust encryption protocols are paramount. Gallagher’s Access Control System leverages advanced encryption to guarantee your data remains secure at all times. Let’s explore the specifics of how this works to protect your assets.
- End-to-End Encryption (E2EE): Data is encrypted on the device before transmission and only decrypted at the endpoint, making sure that even if intercepted, it remains unreadable.
- AES-256 Encryption: Utilizing the Advanced Encryption Standard (AES) with a 256-bit key length, this protocol is considered unbreakable with current technology, providing top-tier security for your data.
- Public Key Infrastructure (PKI): This system uses pairs of cryptographic keys (public and private) to authenticate and secure data exchanges, making certain only authorized entities can access the information.
- TLS/SSL Protocols: Transport Layer Security (TLS) and Secure Sockets Layer (SSL) encrypt data in transit, safeguarding it from eavesdropping and tampering during transmission.
Gallagher’s commitment to employing these advanced encryption protocols guarantees that your access control system not only meets but exceeds industry standards. When you’re responsible for protecting sensitive information, you can’t afford to compromise on encryption strength.
Real-Time Threat Detection
In today’s constantly evolving cyber landscape, real-time threat detection is crucial for maintaining the integrity of your security infrastructure. Gallagher’s access control system excels in this area by leveraging advanced algorithms and machine learning to identify potential threats as they happen. You’ll find that their system continuously monitors network traffic, user behavior, and access patterns to detect anomalies that could indicate a security breach.
The real-time threat detection features are driven by data analytics, which sift through vast amounts of log data to pinpoint irregular activities. For instance, if an unauthorized device attempts to connect to your network, the system can instantly flag and isolate it. This proactive approach minimizes the risk of data breaches and unauthorized access.
Gallagher’s solution also integrates seamlessly with your existing security tools, offering an all-encompassing view of your security posture. Automated alerts and detailed reports provide actionable insights, allowing you to respond swiftly to any potential threats. Furthermore, the system’s scalability guarantees it can handle increasing data loads as your organization grows.
Multi-Factor Authentication
Building on the strengths of real-time threat detection, Gallagher’s access control system also emphasizes robust authentication mechanisms to fortify your cybersecurity defenses. Multi-Factor Authentication (MFA) isn’t just an added layer; it’s a critical component that greatly reduces the risk of unauthorized access.
To give you a clearer picture, here’s how Gallagher’s MFA works:
- Password Authentication: Simple yet vital, a strong password forms the first barrier against intrusions. Gallagher guarantees password policies are stringent, requiring complex combinations that are difficult to crack.
- Biometric Verification: Utilizing fingerprint scans, facial recognition, or iris scans, this method leverages unique biological traits, making sure that only authorized personnel gain access.
- Smart Card Access: These cards are embedded with secure chips that store encrypted data, adding another layer of security. They’re not just swipe-and-go; each card’s data is continuously verified against the system’s database.
- Mobile Authentication: Using mobile devices for MFA adds convenience and security. Gallagher’s system supports push notifications or one-time passwords (OTPs) sent to registered devices, providing real-time verification.
Conclusion
So, you’re now an expert on Gallagher’s access control system components. You know, just the fundamentals like Command Centre Software, biometric readers, and, oh right, real-time monitoring. But don’t worry, it’s not like you require high-security controllers or cyber security features in this day and age, right? Ironically, being data-driven and detail-oriented guarantees you won’t overlook these “minor” elements. After all, who needs scalable systems and mobile access in a tech-driven world?